Cybersecurity tools are software or hardware solutions designed to protect networks, devices, programs, and data from damage, unauthorized access, or cyberattacks. These tools are essential for ensuring confidentiality, integrity, and availability of information—commonly referred to as the CIA triad in cybersecurity.
🔍 Purpose of Cybersecurity Tools
They help in:
- Preventing cyberattacks (e.g., firewalls, antivirus)
- Detecting threats (e.g., IDS/IPS, SIEM)
- Responding to incidents (e.g., forensics, EDR)
- Recovering from breaches (e.g., backup tools, DR systems)
- Ensuring compliance with security standards and regulations
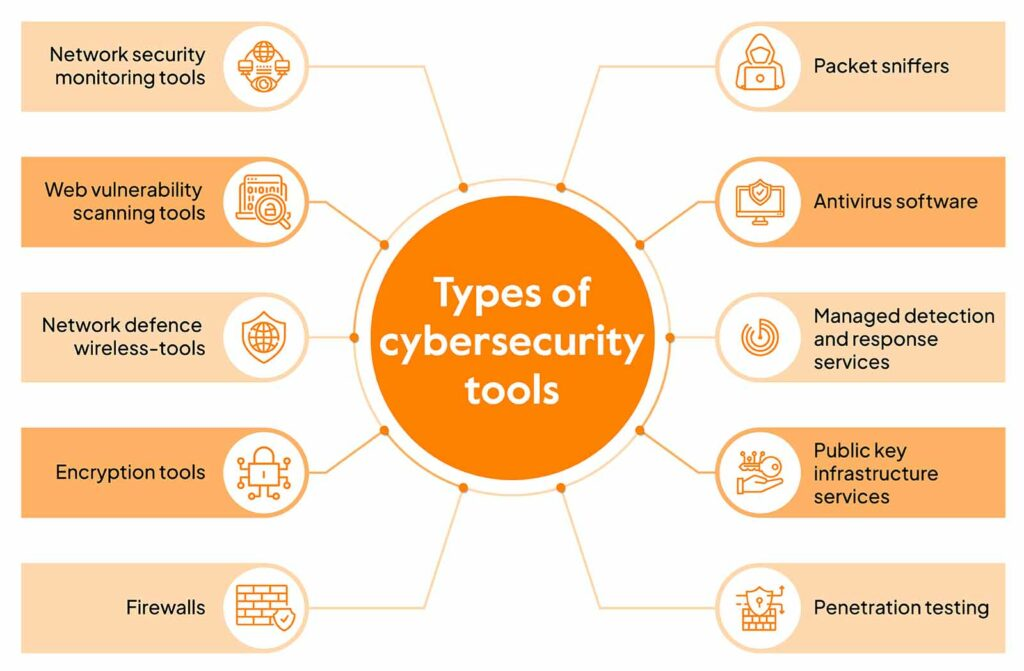
🧰 Types of Cybersecurity Tools
Here’s a breakdown of the main categories:
| Category | Function | Examples |
|---|---|---|
| Firewalls | Block or allow network traffic | pfSense, Cisco ASA |
| Antivirus/Antimalware | Detect and remove malicious software | Bitdefender, ClamAV |
| Intrusion Detection/Prevention (IDS/IPS) | Monitor for suspicious activities | Snort, Suricata |
| SIEM (Security Information & Event Management) | Centralize and analyze security logs | Splunk, QRadar |
| Penetration Testing | Simulate attacks to find vulnerabilities | Metasploit, Nmap |
| Encryption Tools | Protect data using cryptographic methods | GPG, OpenSSL |
| Identity & Access Management (IAM) | Control who can access what | Okta, Azure AD |
| Endpoint Security | Secure devices like laptops and phones | CrowdStrike, SentinelOne |
| Threat Intelligence | Stay informed of new threats | MISP, AlienVault OTX |
| Forensics Tools | Investigate cyber incidents | Autopsy, Volatility |
How Many Cyber Security Tools Are There ?
Here is a comprehensive and detailed list of cybersecurity tools, categorized by their primary purpose. Each tool includes a brief explanation of what it does, its typical use cases, and notable features or examples.
Different types of cybersecurity tools are tailored to counter specific threats. Some of the most popular cybersecurity tools are:
🔐 1. Network Security Tools
Network security monitoring tools are essential for monitoring all traffic flowing through your network. They help you spot potential issues and threats before they escalate into serious problems.
These tools monitor your network in real-time and send instant alerts if they detect anything unusual.
a. Firewalls
- pfSense: Open-source firewall/router software with a web interface. Includes VPN, load balancing, and more.
- Cisco ASA: Advanced hardware-based firewall often used in enterprises.
- IPTables/NFTables: Linux-based firewall tools for traffic filtering and NAT.
b. Intrusion Detection Systems (IDS) / Intrusion Prevention Systems (IPS)
- Snort: Open-source IDS/IPS that analyzes traffic in real time. Rules-based.
- Suricata: Multi-threaded IDS/IPS capable of deep packet inspection, logging HTTP requests.
- OSSEC: Host-based IDS that monitors log files, rootkits, etc.
c. Network Monitoring
- Wireshark: Protocol analyzer for real-time traffic capture and inspection.
- Nagios: Monitors systems, networks, and infrastructure for issues.
- SolarWinds NPM: Commercial network performance monitoring platform.
- PRTG Network Monitor: Monitors uptime, usage, and traffic with sensors.
🛡 2. Endpoint Security Tools
a. Antivirus/Anti-malware
- Bitdefender, Norton, Kaspersky, Sophos: Common endpoint protection software that detects malware and viruses.
- ClamAV: Open-source antivirus engine for detecting trojans, viruses, etc.
b. Endpoint Detection and Response (EDR)
- CrowdStrike Falcon: Real-time endpoint protection with behavioral analysis.
- SentinelOne: AI-based detection, prevention, and response platform.
- Microsoft Defender for Endpoint: Advanced threat protection for Windows environments.
🧰 3. Penetration Testing Tools
a. Frameworks
- Metasploit: A penetration testing framework used for developing and executing exploit code.
- Cobalt Strike: Commercial penetration testing and red-teaming toolkit with beaconing, C2, and post-exploitation.
b. Scanning and Enumeration
- Nmap: Network scanner for host discovery and port scanning.
- Nikto: Web server vulnerability scanner.
- Dirb / Gobuster: URL brute-forcing tools.
c. Exploitation
- ExploitDB: Database of known exploits.
- SQLmap: Automates SQL injection discovery and exploitation.
- Hydra: Fast and flexible password cracker for remote authentication.
d. Wireless Testing
- Aircrack-ng: Suite for auditing Wi-Fi networks.
- Kismet: Wireless network detector, sniffer, and intrusion detection system.
🧬 4. Digital Forensics and Incident Response (DFIR)
a. Disk and Memory Analysis
- Autopsy/The Sleuth Kit: Forensic suite for analyzing disk images.
- Volatility: Memory forensics framework for RAM analysis.
- Magnet AXIOM: Commercial forensic tool that pulls data from devices, cloud, and apps.
b. Log Analysis
- ELK Stack (Elasticsearch, Logstash, Kibana): Centralized logging and analysis.
- Graylog: Open-source log management platform.
🔍 5. Vulnerability Assessment Tools
- OpenVAS (Greenbone): Open-source vulnerability scanner.
- Nessus: Widely used vulnerability scanner with a large plugin database.
- QualysGuard: Cloud-based vulnerability management and compliance tool.
- Burp Suite: Web application scanner and proxy tool.
🧱 6. Application Security Tools
a. Static Application Security Testing (SAST)
- SonarQube: Inspects code for bugs, vulnerabilities, and code smells.
- Checkmarx: Enterprise-grade SAST for various programming languages.
b. Dynamic Application Security Testing (DAST)
- OWASP ZAP: Open-source tool for finding vulnerabilities in running web apps.
- Acunetix: Automated scanner for detecting vulnerabilities in web applications.
c. Software Composition Analysis (SCA)
- Snyk, WhiteSource, Black Duck: Analyze open-source components for vulnerabilities and license compliance.
🔏 7. Encryption and Privacy Tools
- GnuPG (GPG): Encrypt files, emails using public-key cryptography.
- VeraCrypt: Disk encryption software for creating secure containers.
- OpenSSL: Toolkit for implementing SSL/TLS, key generation, and certificate management.
- KeePass / Bitwarden: Password managers with strong encryption.
👤 8. Identity and Access Management (IAM)
- Okta, Azure Active Directory, Auth0: Cloud-based IAM platforms.
- FreeIPA: Open-source identity management system for Linux systems.
- LDAP, Kerberos: Protocols for authenticating users and systems.
🛡 9. SIEM (Security Information and Event Management)
- Splunk: Enterprise-level platform for log aggregation and analysis.
- IBM QRadar: Integrates with various security tools for real-time analysis.
- LogRhythm: Collects logs and correlates security data.
🕵️♂️ 10. Threat Intelligence Platforms
- MISP (Malware Information Sharing Platform): Collaborative threat intelligence platform.
- AlienVault OTX: Open Threat Exchange with community-driven IOCs.
- Recorded Future, Anomali: Commercial platforms for curated threat feeds and insights.
🧱 11. Cloud Security Tools
- AWS GuardDuty / Security Hub: Threat detection and security management in AWS.
- Microsoft Defender for Cloud: Cloud-native security posture management.
- Wiz / Orca Security: Cloud workload protection and vulnerability discovery.
⚙️ 12. Configuration and Compliance Tools
- Lynis: Security auditing for Unix-based systems.
- OpenSCAP: Compliance auditing and vulnerability scanning.
- Tripwire: File integrity monitoring and policy compliance.
🧪 13. Sandboxing and Malware Analysis
- Cuckoo Sandbox: Automated malware analysis system.
- Joe Sandbox: Malware analysis platform supporting various file types.
- Any.Run: Interactive malware sandbox for real-time analysis.
📊 14. Red and Blue Team Tools
- BloodHound: Active Directory analysis for privilege escalation paths.
- MITRE ATT&CK Navigator: Framework for mapping attacker behavior.
- CALDERA: Adversary emulation platform.
- Atomic Red Team: Library of small, testable attack scripts.
Cybersecurity tools are software or hardware solutions designed to protect networks, devices, programs, and data from damage, unauthorized access, or
[See the full post at: Types of Gybersecurity Tools and How Many Cyber Security Tools Are There ?]
Types of Gybersecurity Tools and How Many Cyber Security Tools Are There ?
ICS Tutorial
Related posts:
Related posts: