While cybersecurity professionals aim to keep up with security threats, cyber hackers and attackers are always on the lookout for new ways to evade cybersecurity measures to exploit approaching vulnerabilities. So it’s important to know about some of the most common threats that businesses go through.
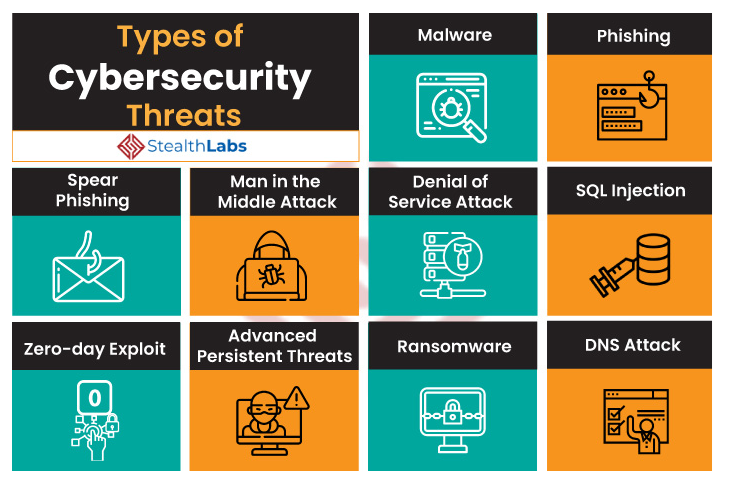
Here are the most common cyber threats organizations and individuals face today, along with brief explanations:
Common Cyber Threats
1. Phishing –
Phishing is one of the social engineering attacks where cyber attackers aim to steal your identity or money by using psychological manipulation to trick you into revealing your sensitive or Personal Identifiable Information.
In simple terms, they will send you an email or message pretending to be a legitimate company and asking for information like login credentials, bank account details, or credit card data.
- What it is: Fraudulent emails or messages tricking users into revealing personal info (e.g., passwords, credit card numbers).
- Example: An email pretending to be from your bank asking you to “verify your account.”
2. Malware –
It refers to malicious software programs (viruses, Trojans, worms, spyware, ransomware, botnets, and Adware) that are intended to cause harm or disruption to the computer networks, system, server, etc to gain unauthorized access to the information.
Typically, malware is spread and installed on the user’s computer via genuine-looking downloads or email attachments.
- What it is: Malicious software like viruses, worms, trojans, spyware, or ransomware that can harm or take control of a device.
- Example: Clicking a fake software download link that installs spyware.
3. Ransomware
Ransomware is a type of malware attack in which the attacker locks or encrypts the victim’s data and threatens to publish or block access to data unless a ransom is paid.
- What it is: A type of malware that encrypts your files and demands payment to restore access.
- Example: The WannaCry attack that spread globally in 2017.
4. Man-in-the-Middle (MitM) Attacks
It is an eavesdropping cyberattack in which a cyberattacker secretly sends and alters communications between two individuals to gain private information while they believe they are communicating with one another.
- What it is: An attacker intercepts communications between two parties to steal or manipulate data.
- Example: Hackers on public Wi-Fi capturing your login info.
5. Denial-of-Service (DoS) / Distributed DoS (DDoS) Attacks
It is a form of cyber threat where the attacker disrupts the traffic of the targeted server by overwhelming it by sending a flood of internet traffic at once. Denial of Service attacks aims at flooding systems, networks, or servers with massive traffic, thereby making the system unable to fulfill legitimate requests. Attacks can also use several infected devices to launch an attack on the target system. This is known as a Distributed Denial of Service (DDoS) attack.
- What it is: Overwhelming a website or server with traffic to make it unavailable.
- Example: A botnet flooding an online store during a big sale.
6. SQL Injection –
It is a form of cyber attack where malicious SQL code is injected into an application to give hackers control over its database and gain access to sensitive information stored there. A Structured Query Language (SQL) injection attack occurs when cybercriminals attempt to access the database by uploading malicious SQL scripts. Once successful, the malicious actor can view, change, or delete data stored in the SQL database. SQL injection accounts for nearly 65.1% of all web application attacks.
- What it is: Attackers insert malicious SQL code into a form input to access or manipulate a database.
- Example: Login bypass via
' OR '1'='1.
7. Zero-Day Exploits
A zero-day attack occurs when software or hardware vulnerability is announced, and the cybercriminals exploit the vulnerability before a patch or solution is implemented.
- What it is: Attacks that exploit unknown or unpatched vulnerabilities in software.
- Example: Hackers using a bug in a browser before developers can fix it.
8. Credential Stuffing
- What it is: Using stolen usernames and passwords (often from leaks) to try logging in to other accounts.
- Example: A hacker using leaked Netflix login info to access your bank.
9. Social Engineering
It is a psychological manipulation technique used by cybercriminals to trick people into making security mistakes leading to revealing their confidential data. Pretexting, Phishing, Tailgating, and CEO fraud are some of the popular examples of social engineering threats.
- What it is: Manipulating people into giving up confidential information.
- Example: A scammer posing as IT support to get your password.
10. Insider Threats
- What it is: Threats from employees or contractors who intentionally or accidentally cause security breaches.
- Example: A disgruntled employee leaking customer data.
11. Brute Force
This attack involves the use of a trial and error method to guess every possible password combination to crack login credentials, passwords, and encryption keys.
12. DNS Attacks
Denial-of-Service attacks that target the availability of network resources and make them temporarily unavailable, disrupting host services. It prevents the computer network or system from functioning properly and fulfilling user requests. A DNS attack is a cyberattack in which cybercriminals exploit vulnerabilities in the Domain Name System (DNS). The attackers leverage the DNS vulnerabilities to divert site visitors to malicious pages (DNS Hijacking) and remove data from compromised systems (DNS Tunneling).
13. Cryptojacking
In cyberjacking, attackers hijack the computer system for mining cryptocurrencies against the will of the user.
14. Advanced Persistent Threats (APTs)
Here a group of intruders hack a system and remain undetected for a long time to keep tabs on business activities and steal sensitive information. They do so by avoiding defensive cybersecurity measures to activate on time. An advanced persistent threat occurs when a malicious actor gains unauthorized access to a system or network and remains undetected for an extended time.
While cybersecurity professionals aim to keep up with security threats, cyber hackers and attackers are always on the lookout for new ways to evade cy
[See the full post at: Top 15 Common Cyber Threats in 2025]
Top 15 Common Cyber Threats in 2025
ICS Tutorial
Related posts:
Related posts: