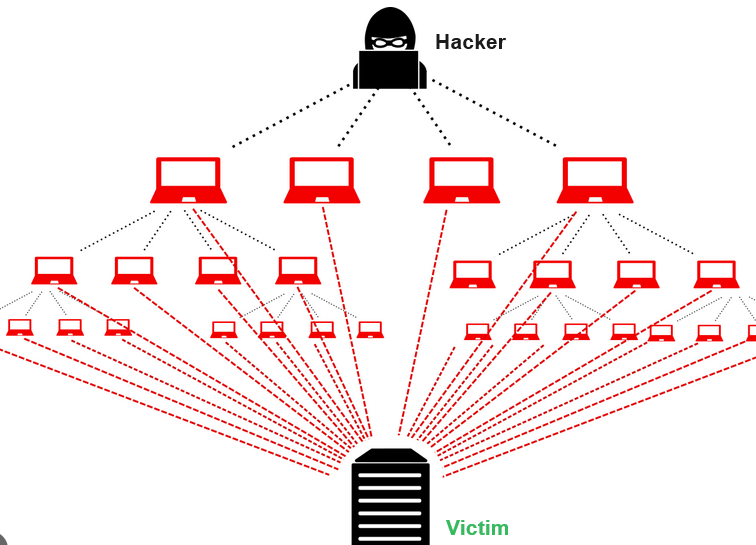
A Distributed Denial of Service (DDoS) attack is a malicious attempt to disrupt the regular functioning of a network, service, or website by overwhelming it with a flood of internet traffic. In a DDoS attack, multiple compromised computers, often referred to as a botnet, are used to flood the target system with traffic, causing it to become slow, unresponsive, or completely unavailable to users.
The key characteristics of a DDoS attack include:
- Distributed Nature: DDoS attacks involve multiple sources (computers or devices), making it difficult to trace and mitigate the attack.
- Denial of Service: The primary goal is to deny access to a particular service, server, or network resource, rendering it inaccessible to legitimate users.
- Volume of Traffic: DDoS attacks typically involve a massive volume of traffic that overwhelms the target system’s capacity to handle requests.
- Variety of Techniques: Attackers use various techniques, such as sending a high volume of requests, exploiting vulnerabilities, or using amplification methods to magnify the impact of the attack.
- Botnets: Many DDoS attacks are carried out using a network of compromised computers (botnet), which are often controlled remotely by the attacker.
The motives behind DDoS attacks can vary. They may be carried out for financial gain, revenge, competition, or simply for the purpose of causing disruption and chaos. Organizations and individuals often deploy various security measures, such as firewalls and DDoS mitigation services, to protect against these types of attacks.
Types of DDoS Attacks
Distributed Denial of Service (DDoS) attacks come in various forms, each with its own characteristics and methods. Here are some common types of DDoS attacks:
- Volume-Based Attacks:
- UDP Flood: The attacker floods the target with a large number of User Datagram Protocol (UDP) packets, overwhelming the target’s bandwidth.
- ICMP Flood: Attackers use a large number of Internet Control Message Protocol (ICMP) packets to flood the target, causing network congestion.
- Protocol-Based Attacks:
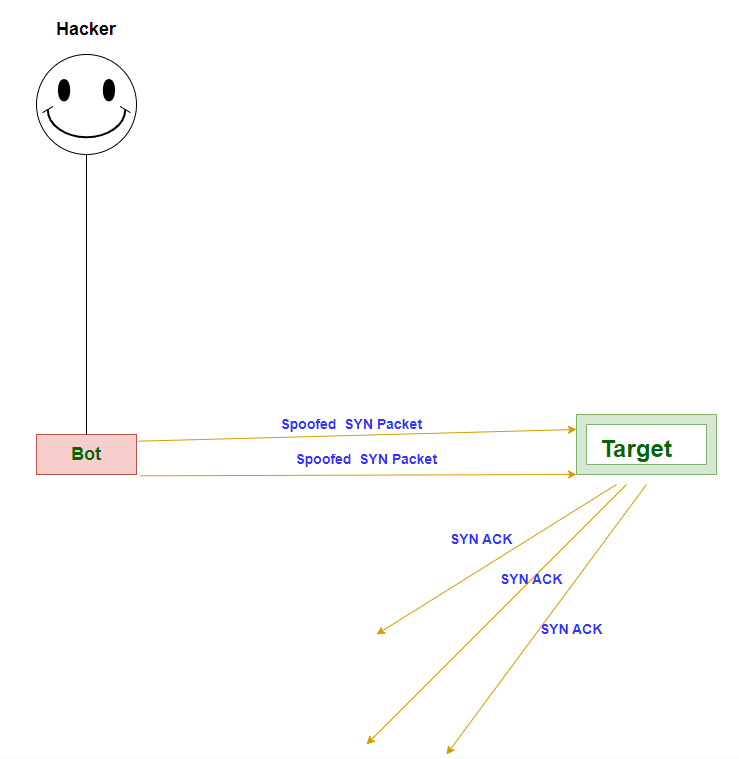
- SYN/ACK Flood: Exploits the TCP handshake process by sending a large number of SYN requests without completing the handshake, consuming server resources.
- HTTP Flood: Overwhelms a web server by sending a large volume of HTTP requests, exhausting server resources and causing it to become slow or unresponsive.
- Application Layer Attacks:
- HTTP/HTTPS Flood: Similar to an HTTP flood but specifically targeting the application layer of a web server, aiming to exhaust server resources.
- Slowloris Attack: Exploits the way web servers handle connections by keeping numerous connections open but sending data very slowly, preventing them from being reused.
- Reflective/Amplification Attacks:
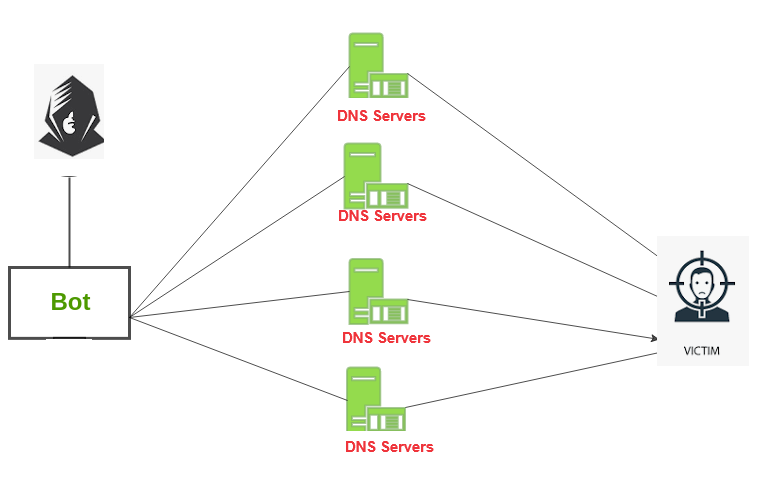
- DNS Amplification: Utilizes open DNS servers to flood the target with DNS response traffic, amplifying the attack’s volume.
- NTP Amplification: Exploits Network Time Protocol (NTP) servers to overwhelm the target with amplified traffic.
- Volumetric Attacks:
- BitTorrent DDoS: Exploits BitTorrent protocols to amplify the traffic and overwhelm the target’s network.
- Application Exploitation Attacks:
- Zero-Day Exploits: Targets vulnerabilities in software applications or systems that are not yet known to the vendor, taking advantage of the time gap before a patch is released.
- IoT-Based Attacks:
- IoT Botnets: Compromised Internet of Things (IoT) devices are used to create large botnets, capable of executing powerful DDoS attacks.
- DNS Spoofing and Cache Poisoning:
- DNS Spoofing: Redirects DNS requests to malicious servers.
- Cache Poisoning: Injects false information into a DNS resolver’s cache.
DDoS attacks are continually evolving, and attackers often combine multiple techniques to maximize their impact. Organizations employ various DDoS mitigation strategies, including traffic filtering, rate limiting, and the use of content delivery networks (CDNs) to protect against these threats.
How to Identify a DDoS Attack ?
Identifying a Distributed Denial of Service (DDoS) attack can be challenging, but there are several signs and symptoms that may indicate such an attack is occurring. Here are some common indicators that can help you identify a DDoS attack:
- Unusual Network Traffic Patterns:
- A sudden and significant increase in network traffic, especially if it is incoming traffic, may indicate a DDoS attack. This surge in traffic can overwhelm network bandwidth and impact the normal flow of legitimate requests.
- Network Performance Issues:
- Degraded network performance, such as slow response times, increased latency, or intermittent service disruptions, can be indicative of a DDoS attack. Users may experience difficulties accessing websites or online services.
- Unusual Server Behavior:
- Increased resource utilization on servers, such as high CPU or memory usage, may be a sign of a DDoS attack. This occurs as the target system struggles to handle the excessive volume of incoming requests.
- Downtime or Unavailability:
- If a website or online service experiences unexpected downtime or becomes completely unavailable, it may be due to a DDoS attack overwhelming the system’s capacity.
- Inability to Access Specific Resources:
- Users may report difficulties accessing specific pages, services, or applications within a website. This can be a targeted effect of a DDoS attack aimed at a particular part of the infrastructure.
- Unexpected Error Messages:
- Increased occurrences of error messages, such as “server unavailable” or “connection timed out,” may suggest a DDoS attack affecting the availability of the targeted service.
- Anomalous Traffic Sources:
- Monitoring network traffic and identifying unexpected or suspicious sources of traffic can help in detecting a DDoS attack. Look for patterns that deviate from normal traffic behavior.
- Unusual Patterns in Web Server Logs:
- Analyzing web server logs may reveal unusual patterns or a high number of requests coming from specific IP addresses. DDoS attacks often involve a large number of requests from multiple sources.
- Increased Number of Security Alerts:
- Security monitoring systems, intrusion detection/prevention systems, or DDoS mitigation services may generate alerts when abnormal traffic patterns or attack signatures are detected.
- Communication from Attackers:
- In some cases, attackers may issue threats or demands before launching a DDoS attack. Monitoring communication channels and being aware of potential threats can provide advanced warning.
What are Common DDoS Attacks ?
Common DDoS (Distributed Denial of Service) attacks encompass various techniques and strategies that malicious actors employ to overwhelm and disrupt the target’s services. Here are some of the most common types:
- UDP Flood:
- Description: Overloads the target’s network by sending a large number of User Datagram Protocol (UDP) packets.
- Impact: Consumes available bandwidth, causing network congestion.
- TCP SYN/ACK Flood:
- Description: Exploits the TCP handshake process by sending a flood of SYN or ACK packets without completing the handshake.
- Impact: Exhausts server resources and can lead to service disruption.
- HTTP/HTTPS Flood:
- Description: Overwhelms a web server with a massive volume of HTTP or HTTPS requests.
- Impact: Exhausts server resources, making the website slow or unresponsive.
- ICMP (Ping) Flood:
- Description: Floods the target with Internet Control Message Protocol (ICMP) ping requests.
- Impact: Can cause network congestion and disrupt legitimate traffic.
- DNS Amplification:
- Description: Exploits open DNS servers to amplify traffic by generating a large number of DNS response packets.
- Impact: Overwhelms the target with amplified traffic.
- NTP Amplification:
- Description: Utilizes Network Time Protocol (NTP) servers to amplify attack traffic.
- Impact: Increases the volume of traffic directed at the target.
- Slowloris Attack:
- Description: Exploits the way web servers handle connections by keeping numerous connections open but sending data very slowly.
- Impact: Exhausts server resources by holding connections open for an extended period.
- Smurf Attack:
- Description: Spoofs the source address of ICMP ping requests to create a flood of responses directed at the victim.
- Impact: Overwhelms the target’s network with amplified traffic.
- Application Layer Attacks:
- Description: Target vulnerabilities in specific applications or services, causing them to become unresponsive.
- Examples: SQL injection attacks, Cross-Site Scripting (XSS), and application-specific exploits.
- IoT-Based Botnet Attacks:
- Description: Compromised Internet of Things (IoT) devices are used to create large botnets, capable of executing powerful DDoS attacks.
- Impact: Increased scale and complexity of DDoS attacks.
These attacks can be executed individually or in combination, making it challenging for organizations to defend against them.
DDoS Mitigation
DDoS mitigation refers to the strategies and techniques used to minimize or prevent the impact of Distributed Denial of Service (DDoS) attacks on a network, service, or website. DDoS attacks are intended to overwhelm and disrupt the normal functioning of a target by flooding it with a large volume of traffic. Mitigation measures aim to identify and filter out malicious traffic, allowing legitimate users to access the services without interruption. Here are common DDoS mitigation techniques:
- Traffic Filtering:
- Identify and filter out malicious traffic based on various attributes such as IP addresses, packet types, or unusual patterns.
- Use firewalls and intrusion prevention systems (IPS) to block or allow traffic based on predefined rules.
- Rate Limiting:
- Implement rate limiting mechanisms to restrict the number of requests from a single source or within a specified time frame.
- This helps prevent the network or server from being overwhelmed by a high volume of requests.
- Anomaly Detection:
- Employ anomaly detection systems to identify deviations from normal network behavior.
- Unusual spikes in traffic or patterns that deviate from baseline behavior can trigger alerts or automatic mitigation responses.
- Content Delivery Networks (CDNs):
- Distribute content across multiple servers and locations to improve performance and resilience.
- CDNs can absorb and mitigate DDoS attacks by distributing traffic and caching content closer to end-users.
- Cloud-Based DDoS Protection:
- Use cloud-based DDoS protection services that can absorb and filter out malicious traffic before it reaches the target’s network.
- These services often have large-scale infrastructure and specialized tools to handle DDoS attacks.
- Load Balancers:
- Distribute incoming network traffic across multiple servers to ensure no single server becomes overwhelmed.
- Load balancers can help distribute the load during a DDoS attack, preventing a single point of failure.
- Behavioral Analysis:
- Analyze the behavior of incoming traffic to distinguish between legitimate and malicious requests.
- Behavioral analysis can help identify patterns associated with DDoS attacks and trigger appropriate responses.
- Collaborative DDoS Protection:
- Share threat intelligence and collaborate with other organizations or service providers to collectively defend against DDoS attacks.
- Collective efforts can enhance the ability to identify and mitigate evolving DDoS threats.
Implementing a combination of these mitigation techniques provides a more robust defense against DDoS attacks. Organizations often tailor their DDoS protection strategies based on their specific needs, the nature of their services, and the potential threats they face.